Ultimate Guide to Encryption Methods

Encryption is a method of securing information. It converts readable data into secret code. Only the right key can decode it. This guide will help you understand different encryption methods.
How is Your Cyber Hygiene? Essential Tips For 2025
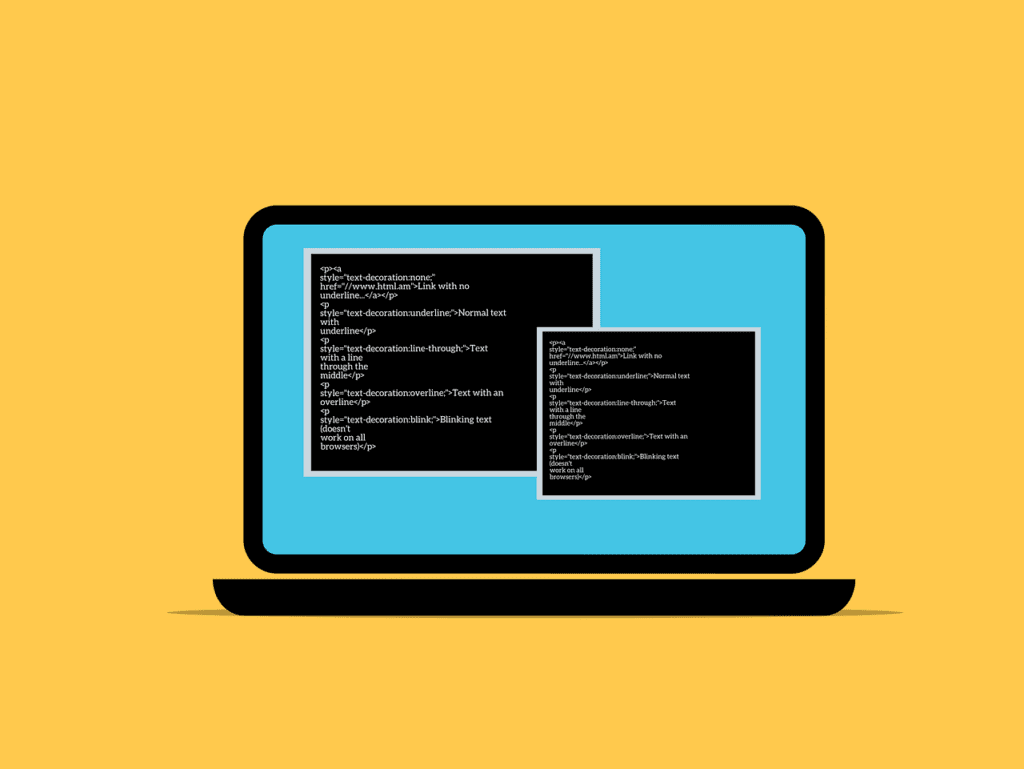
Encryption is a method of securing information. It converts readable data into secret code. Only the right key can decode it. This guide will help you understand different encryption methods.
What is Threat Exposure Management (TEM)?

Threat Exposure Management (TEM) is an important cybersecurity tool. It helps organizations find and fix weak spots in their digital systems. TEM outsmarts hackers before they break into your network.
How Password Managers Protect Your Accounts

Passwords unlock our digital lives. We use them for email, bank accounts, and more.
Remembering all these passwords is hard. Password managers help us keep our accounts safe and make our lives easier.
Innovative Solutions to IoT Device Security

The Internet of Things is growing day by day. More devices are connecting to the internet. And with that growth comes new security risks.
Let’s look at some new ways to keep your IoT devices safe.
Protect Yourself: 8 Steps to Take When You Get a Notice Your Data Was Breached

When it happens, you feel powerless. You get an email or letter from a business saying someone breached your data. It happens all too often today. Data breaches happen at banks, online sites like Facebook, and ecommerce stores. Not only that, but governments are also victims. This leaves things like your address, SSN, and credit […]
Watch Out for Google Searches – “Malvertising” Is on the Rise!
There are many types of malware. One of the most common is called “malvertising.” It crops up everywhere. Including social media sites and websites. You can also see these malicious ads on Google searches. Two things are making malvertising even more dangerous. One is that hackers use AI to make it very believable. The other […]
Cyber Experts Say You Should Use These Best Practices for Event Logging
Today’s businesses are no stranger to the word cybersecurity. They are facing a growing wave of cyberattacks. These come from ransomware to sophisticated phishing schemes. How do you stand ahead of these threats? A strong cybersecurity strategy is essential. One crucial component of this strategy is event logging. It’s one that not every business owner […]
6 Simple Steps to Enhance Your Email Security

Email is a fundamental communication tool for businesses and individuals alike. But it’s also a prime target for cybercriminals. Cyberattacks are increasing in sophistication. This means enhancing your email security has never been more critical. Ninety-five percent of IT leaders say cyberattacks have become most sophisticated. Over half (51%) have already seen AI-powered attacks in […]
Don’t Be a Victim: Common Mobile Malware Traps

Your smartphone is a digital wallet, communication hub, and personal assistant. All rolled into one portable device. It’s packed with sensitive data, from financial information to personal photos. This makes it a prime target for cybercriminals. Mobile malware is often overlooked. People focus on securing their laptops or desktops. But they don’t pay as close […]
